Researchers demo ransomware attack on DSLR cameras
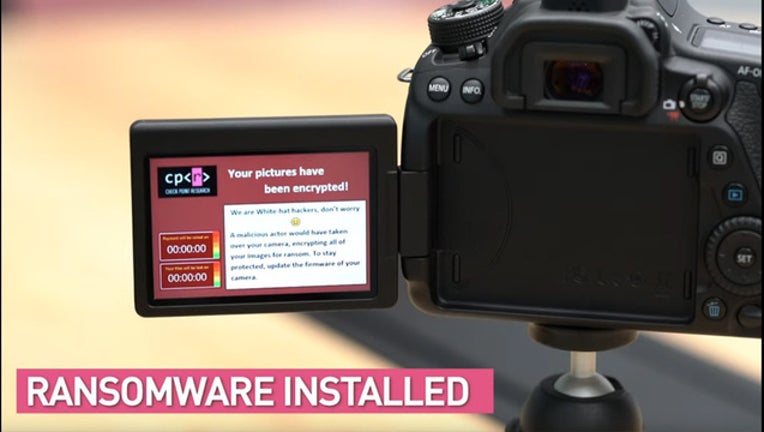
Security researchers stage a proof of concept ransomware attack on a Canon EOS 80D DSLR camera. Photo: Check Point Research
San Jose, Calif. (KTVU) - Ransomware - one of the most popular forms of destructive malware – typically encrypts data on a host's computer and demands ransom, usually in crypto currency. These attacks have traditionally occurred on computer networks, though researchers at Check Point Research recently demonstrated an attack that infects digital cameras.
The attack relies on the Picture Transfer Protocol, used by cameras to transfer pictures and perform a number of other operations, and uses USB and WiFi as attack vectors. The researchers chose to focus on Canon's cameras, due to its popularity, connectivity support for Wi-Fi and USB, and support for firmware add-ons such as Magic Lantern.
"Attackers are profit-maximizers, they strive to get the maximum impact (profit) with minimal effort (cost)," writes Check Point security researcher Eyal Itkin in a blog post demonstrating the attack. "In this case, research on Canon cameras will have the highest impact for users, and will be the easiest to start, thanks to the existing documentation created by the ML (Magic Lantern) community."
The researchers have published a video demonstrating how they used a rogue WiFi access point to deploy the ransomware, which encrypts the photos on the camera's SD card.
Canon has published a security advisory acknowledging the vulnerability, and suggesting potential workarounds – which include updating the firmware, avoiding unsecured networks, turning off a camera's network functions, and not pairing it with infected PC or mobile devices.
Similar vulnerabilities exist in PTP implementations of other vendors as well, the researchers say, adding that, any "smart" device is susceptible to such an attack.

